Digital Forensics
*********
*********
II. Digital Evidence
-Learn Linux
*********
*********
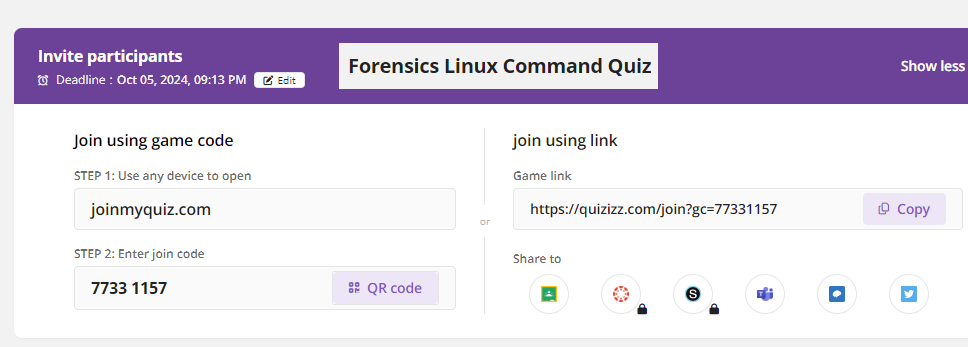
Due Date: September 13, 2024
Linux Permission for files and directories Assignment
Linux Permissions Using chmod and Octal Numbers
In Linux, file permissions are a way to control who can read,
write, or execute a file or directory.
The chmod command is used to change the permissions of a
file or directory, often represented in an octal (numeric) format.
Your task is to take notes on the use of the permission
command chmod based on Mr. Cusack's instructions.
You will write the notes displayed on the board onto paper,
ensuring that you include a standard heading.
Name your file as follows: PX_LinuxPermissions_lastname.png.
Once completed, submit a photo of your notes to Google Classroom.
Read my notes below:
File Permissions Overview
Each file or directory has three sets of permissions, corresponding to three groups:
1. Owner (User): The person who owns the file.
2. Group: Other users who belong to the file's group.
3. Others (World): All other users on the system.
Each set has three types of permissions:
- Read (r): Ability to view the file's content.
- Write (w): Ability to modify the file's content.
- Execute (x): Ability to run the file (if it's a script or program) or access a directory.
Octal Numbers in chmod
Each of the three permissions (read, write, execute) is represented by a number:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
- No permission (-) = 0
To represent permissions in octal form, you sum the values for each group of permissions (owner, group, others).
Examples of Octal Permissions
Examples:
- rwx = 4 + 2 + 1 = 7 (read, write, execute)
- rw- = 4 + 2 + 0 = 6 (read, write, no execute)
- r-- = 4 + 0 + 0 = 4 (read-only)
So, a three-digit octal number defines the permissions for owner, group, and others. For example:
- 755:
- Owner: rwx (4 + 2 + 1 = 7)
- Group: r-x (4 + 0 + 1 = 5)
- Others: r-x (4 + 0 + 1 = 5)
This means the owner can read, write, and execute the file, while the group and others can only read and execute it.
Using chmod with Octal Numbers
The chmod command is used to set these permissions. For example:
chmod 755 filename
This sets the permissions so that:
- The owner can read, write, and execute.
- The group can read and execute.
- Others can read and execute.
Common Permission Codes:
- 777: Everyone can read, write, and execute.
- 755: Owner has full permissions, others can read and execute.
- 644: Owner can read and write, others can only read.
- 600: Only the owner can read and write.
Changing Permissions with Symbolic Mode
You can also use symbolic notation:
- chmod u+rwx adds read, write, and execute permissions for the owner (user).
- chmod g-w removes write permission from the group.
- chmod o+x adds execute permission for others.
This approach allows more granular control without using octal numbers.
*********
*********
Due Date: August 9, 2024
Purpose: To expand/review your knowledge of Linux Part A
Assignment:
-Start your Cyber range
-Get paper
-Insert your standard heading
-Follow Mr. Cusack's lecture instruction.
Linux commands Definitions:
1. ssh: Stands for Secure Shell. It is a protocol used to securely connect to a remote server or
computer over a network. It provides a secure channel over an unsecured network by using
cryptographic techniques.
2. ls: Lists the contents of a directory. It can display files, directories, and other types of files in the
current directory or a specified directory, and it supports various options to control the output format.
3. pwd: Stands for Print Working Directory. It displays the current directory that you're in, showing
the full path from the root directory.
4. cd ..: Changes the current directory to the parent directory. 'cd' stands for Change Directory, and
'..' represents the parent directory.
5. touch: Primarily used to create empty files and can also be used to change the timestamps of a
file (access time, modify time). If the specified file does not exist, it creates a new empty file.
6. echo: Used to display a line of text/string that is passed as an argument. It is commonly used in
scripting and batch files to output status text to the screen or a file.
7. nano: A simple, user-friendly text editor for Unix and Linux operating systems. It's used for
creating and editing text files directly within the terminal.
8. Vim: An advanced text editor that is a more powerful version of the Unix 'vi' editor. It is used for
editing any kind of text and is especially suited for editing computer code.
9. cat: Stands for concatenate. It reads data from files and outputs their contents. It is commonly
used to display the contents of a file on the screen.
10. shred: Used to securely delete files from the disk by overwriting them with random data, making
it very difficult to recover the data.
11. mkdir: Stands for Make Directory. It is used to create new directories.
12. cp: Stands for copy. It is used to copy files or directories from one location to another.
13. mv: Stands for move. It is used to move or rename files or directories from one location to
another.
14. echo Full name - Today's Date: Month day, year - Part A
Purpose: To expand/review your knowledge of Linux Part A
Title: "60 commands Part A".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Fundamentals
60 Linux Commands you NEED to know (in 10 minutes) - Click here https://youtu.be/gd7BXuUQ91w?si=yDXRCCMuSyDAwBTn
10:49
File Names:
P1_60commandsPrtA_paper_lastname.png (Picture of your notes)
P1_60commandsPrtA_History_lastname.png (Screen print of your History)
P1_60commandsPrtA_History_lastname.mp4 (Video with your voice explaining commands)
You will need to drop off a copy of you paper
and a copy of your history into google classroom.
*********
*********
Due Date: September 10, 2023
Purpose: To expand/review your knowledge of Linux commands Part B
Assignment:
-Start your Cyber range
-Get paper
-Insert your standard heading
-Follow Mr. Cusack's lecture instruction on Linux commands Examined
Linux commands Definitions:
1. sudo apt-get install pacman4console: Installs
the game Pacman for the console from the package
repositories using the Advanced Package Tool (APT).
sudo elevates privileges to allow installation.
2. finger: A utility that displays information
about system users. sudo apt install finger installs the
finger utility if it's not already installed.
3. sudo: A command that allows permitted users
to execute a command as the superuser or another
user, as specified by the security policy.
4. adduser: A command to add a new user to the
system, usually requiring sudo to execute with
administrative privileges.
5. man: Displays the manual pages for commands,
showing detailed documentation about how to
use that command.
6. whatis: Displays a one-line description of a
command, giving a quick idea of what the command
does.
7. which: Shows the full path of shell commands,
helping to identify where a command is located.
8. where (possibly meant whereis): whereis locates
the binary, source, and manual page files for a
command.
9. wget: A non-interactive network downloader,
allowing for direct file downloads from the internet
10. curl: A tool to transfer data from or to a
server with supported protocols (HTTP, HTTPS, FTP,
etc.), capable of uploading data as well.
11. clear: Clears the terminal screen, effectively
making it look as if you had just opened a new
terminal window.
12. history: Displays the command history,
showing a list of commands previously entered in the
current terminal session.
13. echo Full name - Today's Date: Month day, year - Part B
Title: "60 commands Part B".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Fundamentals
60 Linux Commands you NEED to know (in 10 minutes) - Click here https://youtu.be/gd7BXuUQ91w?si=yDXRCCMuSyDAwBTn
10:49
File Names:
P1_60commandsPrtB_paper_lastname.png (Picture of your notes)
P1_60commandsPrtB_History_lastname.png (Screen print of your History)
P1_60commandsPrtB_History_lastname.mp4 (Video with your voice explaining commands)
You will need to drop off a copy of you paper
and a copy of your history into google classrom.
*********
*********
Date: September 12, 2024
Purpose: To expand your knowledge of Linux commands Part C
Assignment:
-Start your Cyber range
-Get paper
-Insert your standard heading
-Follow Mr. Cusack's lecture instruction on Linux commands Examined
Linux commands Definitions:
1. zip: Compresses files and directories into a zip archive, reducing file size and combining multiple
items into a single file for easier handling.
2. unzip: Extracts files from a zip archive, restoring compressed files to their original state.
less: Allows for paging through text one screen at a time, useful for viewing large files by navigating
forwards and backwards without loading the entire file.
3. head: Outputs the first part of files, typically used to display the start of a file. By default, displays the
first 10 lines unless otherwise specified.
4. tail: Displays the last part of files, often used to view the most recent entries in log files. By default,
shows the last 10 lines.
5. cmp: Compares two files byte by byte and reports the first discrepancy, if any, useful for checking if
two files are identical.
6. diff: Compares files line by line and outputs the differences between them, commonly used to show
changes between two versions of the same file.
7. sort: Sorts the lines of text in the specified files in alphabetical, numerical, reverse order, and can
also remove duplicates if specified.
8. find: Searches the directory tree from a given starting point, evaluating expressions to match files
and directories.
9. chmod: Changes the file system modes of files and directories, including permissions and other
special modes.
10. chown: Changes the user and/or group ownership of given files or directories.
11. ifconfig: Used for network interface configuration, including initializing an interface, assigning IP
addresses, and enabling or disabling interfaces. While deprecated in favor of the ip command in
most modern systems, it remains in use for specific network configuration tasks.
12. echo Full name - Today's Date: Month day, year - Part C
Title: "60 commands Part C".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Fundamentals
60 Linux Commands you NEED to know (in 10 minutes) - Click here https://youtu.be/gd7BXuUQ91w?si=yDXRCCMuSyDAwBTn
10:49
File Names:
P1_60commandsPrtC_paper_lastname.png (Picture of your notes)
P1_60commandsPrtC_History_lastname.png (Screen print of your History)
P1_60commandsPrtC_History_lastname.mp4 (Video with your voice explaining commands)
You will need to drop off a copy of you paper
and a copy of your history into google classroom.
*********
*********
*********
*********
*********
*********
Due Date: September 23, 2024
Purpose: To build your skills in using the APT package manager.
- You need to step thru each slide and execute them in
- The cyber range.
- After completing this, I will provide further instructions.
Click here and follow the instructions.
Use your cyber range.
*********
*********
Due Date: September 24, 2024
You must complete the APT assignment above
before doing this.
Purpose: To build learn how to use the CyberChef.
Click here and review the instructions.
Click here to access CyberChef.
https://gchq.github.io/CyberChef/
*********
*********
*********
Resources you may need (Below)
*********
*********
*********
*********
*********
*********
*********
**********
**********
**********
**********
**********
**********
**********
**********
**********
**********
**********
**********
**********
**********
Course Outline:
I. Introduction to Digital Forensics
- Definition and scope of digital forensics
- History and evolution of digital forensics
- Importance of digital forensics in law enforcement and cybersecurity
- Types of digital forensics: computer, network, mobile, and cloud
- Legal and ethical considerations
II. Digital Evidence
-Learn Linux
-Types of digital evidence
-Collection and preservation of digital evidence
-Chain of custody
III. Digital Crime and Cybersecurity
-Types of digital crimes (e.g. hacking, identity theft)
-Common cybersecurity threats (e.g. malware, phishing)
IV. Computer Systems and Networks
-Basic computer architecture and operating systems
-Computer networks and network protocols
-Network security and intrusion detection
V. Linux
-File systems and partitions
https://cyber.instructure.com/courses/357
Unit 1 - FSH, Using CLI &s; File Editing
Unit 1 Lesson Plan
-1.1.1 - File System Hierarchy Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-1.2.5 - File and Directory Management Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Linux 101 Quiz : Key
-3.1.1 - Shell Script Elements Part 1 Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-3.1.2 - Shell Script Elements Part 2 Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-1.2.1 - File Editing Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Nano vs Vim Quiz : Key
-3.1.3 - Script Utilities and Variables Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Linux 102 Quiz : Key
-1.2.3 - Metadata Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-1.2.2 - File Compressing and Archiving Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - File Compression and Metadata Quiz : Key
Unit 2 - User Accounts &s; Management
Unit 2 Lesson Plan
-2.2.1 - Account Creation and Deletion Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Account Creation Quiz : Key
-2.2.2 - Account Configuration and Management Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-2.4.2 - Executing Commands as Another User Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - To sudo or Not to sudo, That Is the Question Quiz : Key
-4.4.1 - Troubleshooting File Permissions Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Troubleshooting File Permissions Quiz : Key
Unit 3 - Services &s; Networking
Unit 3 Lesson Plan
-1.4.1 - System Services Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-1.4.2 - Process Management Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-1.5.1 - Network Interface Management Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-1.5.2 - Name Resolution Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
-1.5.3 - Network Monitoring Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - TCPDUMP vs Wireshark Quiz : Key
-1.5.4 - Remote Networking Tools Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Remote Networking Tools Quiz : Key
-1.2.4 - Linking and Copying Files Between Systems Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Linking and Copying Files Between Systems Quiz : Key
-4.2.1 - Network Resource Issues Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Nmap and nslookup Quiz : Key
VI. Computer Forensics
-Data recovery and analysis
-File systems and partitions
Linux
Steganography and cryptography
VII. Network Forensics
Network traffic analysis
Network protocols and packet analysis
Investigating network intrusions
VIII. Presentation and Reporting
Documenting and reporting findings
Testifying in court
IX. Mobile Device Forensics
Types of mobile devices and operating systems
Collection and analysis of mobile device data
X. Emerging Trends in Digital Forensics
New technologies and techniques in digital forensics
Current issues and challenges in digital forensics
Note that this is just a sample outline and actual course content
and order may vary depending on the specific high school program and instructor.
It's important to ensure that students have a strong work ethic.
**********
**********
*********
*********