Cyber Capstone
Unit 1 (Cyber.org https://cyber.instructure.com/courses/100)
*********
*********
Due Date: September 13, 2024
Linux Permission for files and directories Assignment
Linux Permissions Using chmod and Octal Numbers
In Linux, file permissions are a way to control who can read,
write, or execute a file or directory.
The chmod command is used to change the permissions of a
file or directory, often represented in an octal (numeric) format.
Your task is to take notes on the use of the permission
command chmod based on Mr. Cusack's instructions.
You will write the notes displayed on the board onto paper,
ensuring that you include a standard heading.
Name your file as follows: PX_LinuxPermissions_lastname.png.
Once completed, submit a photo of your notes to Google Classroom.
Read my notes below:
File Permissions Overview
Each file or directory has three sets of permissions, corresponding to three groups:
1. Owner (User): The person who owns the file.
2. Group: Other users who belong to the file's group.
3. Others (World): All other users on the system.
Each set has three types of permissions:
- Read (r): Ability to view the file's content.
- Write (w): Ability to modify the file's content.
- Execute (x): Ability to run the file (if it's a script or program) or access a directory.
Octal Numbers in chmod
Each of the three permissions (read, write, execute) is represented by a number:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
- No permission (-) = 0
To represent permissions in octal form, you sum the values for each group of permissions (owner, group, others).
Examples of Octal Permissions
Examples:
- rwx = 4 + 2 + 1 = 7 (read, write, execute)
- rw- = 4 + 2 + 0 = 6 (read, write, no execute)
- r-- = 4 + 0 + 0 = 4 (read-only)
So, a three-digit octal number defines the permissions for owner, group, and others. For example:
- 755:
- Owner: rwx (4 + 2 + 1 = 7)
- Group: r-x (4 + 0 + 1 = 5)
- Others: r-x (4 + 0 + 1 = 5)
This means the owner can read, write, and execute the file, while the group and others can only read and execute it.
Using chmod with Octal Numbers
The chmod command is used to set these permissions. For example:
chmod 755 filename
This sets the permissions so that:
- The owner can read, write, and execute.
- The group can read and execute.
- Others can read and execute.
Common Permission Codes:
- 777: Everyone can read, write, and execute.
- 755: Owner has full permissions, others can read and execute.
- 644: Owner can read and write, others can only read.
- 600: Only the owner can read and write.
Changing Permissions with Symbolic Mode
You can also use symbolic notation:
- chmod u+rwx adds read, write, and execute permissions for the owner (user).
- chmod g-w removes write permission from the group.
- chmod o+x adds execute permission for others.
This approach allows more granular control without using octal numbers.
*********
*********
*********
*********
Due Date: September 9, 2024
D2.4.14 Password Attacks
D2.4.14 Password Attacks - Lesson Notes - Read this.
D2.4.14 Password Attacks - Read this.
Copy the document found below into a google document
under your class directory.
Answer the questions in your google document.
Highlight the answer in yellow.
Name the the google document "D2.4.14 Password Attacks Guided Notes"
Title: "Password Attacks".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Capstone
D2.4.14 Password Attacks Guided Notes Answer this - Click here.
Copy the document found below into a google document
under your class directory.
Answer the questions in your google document.
Highlight the answer in yellow.
Name the the google document "D2.4.14 Password Attacks lastname quiz"
Title: "Quiz Password Attacks".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Capstone
D2.4.14 Password Attacks quiz Answer this - Click here.
*********
*********
Due Date: September 10, 2024
D2.4.14LAB Password Salt
Click here and follow the Lab instructions.
As you follow the instructions and get to page 14:
This is what page 14 should look like:
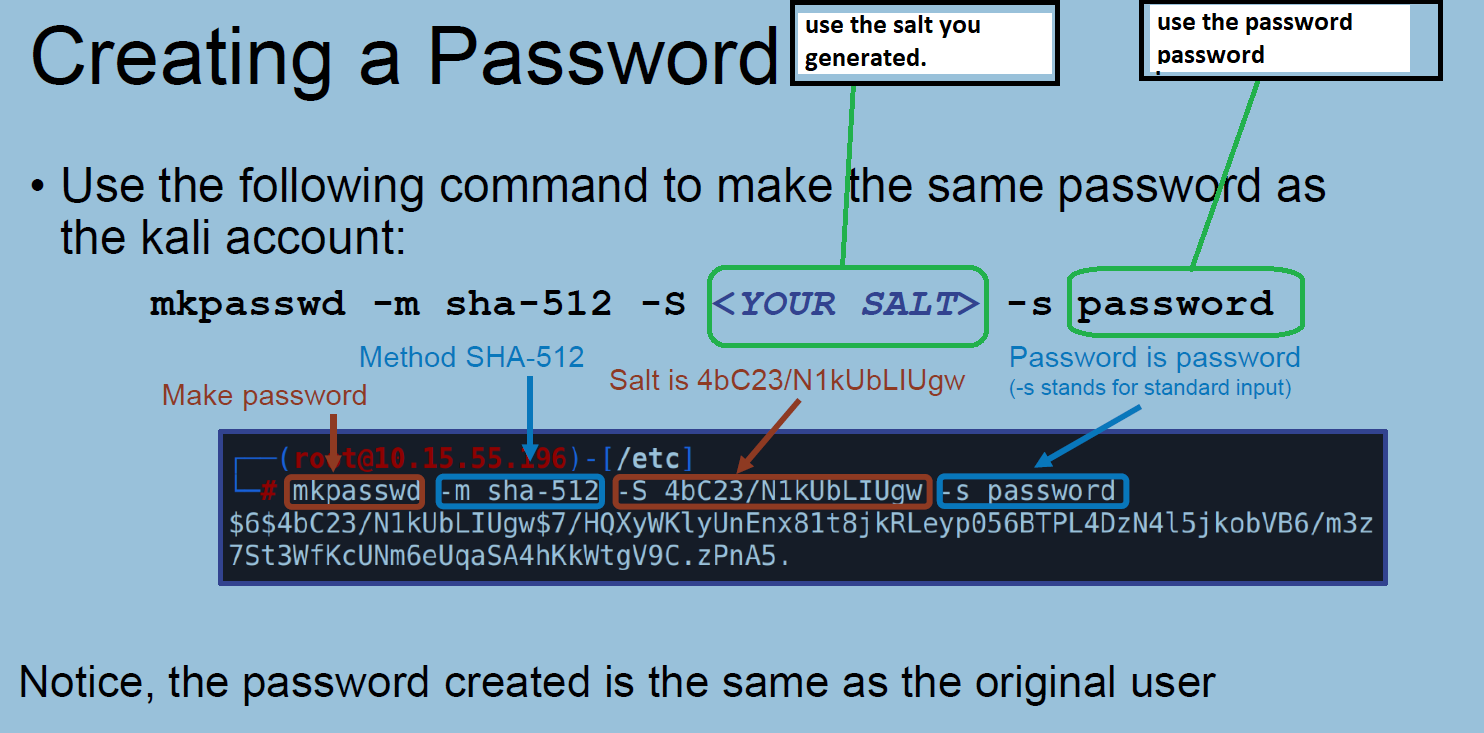
Use your last name for the salt.
Screen print what your screen looks like.
Save the file as PX_lastname_passwordSalt.png
When you complete the assignment,
Enter the command of History.
Screen print the results.
Save the file as PX_lastname_HistoryPasswordSalt.
Drop off both files into google classroom.
*********
*********
Due Date: September 11, 2024
D2.4.14LAB Rainbow Table
Click here and follow the Lab instructions.
Follow the instructions below:
On page 11, if the rtgen does not work
Run the following install sudo-get install rainbowcrack
On page 12,
When you run echo -n "david" | md5sum
replace david with your first name
repeat the command echo "david" | md5sum
with a different first names from your family
When the hashs are seen screen print it.
Save the file as PX_lastname_RainbowCrack.png
See example of hash image on the next line.
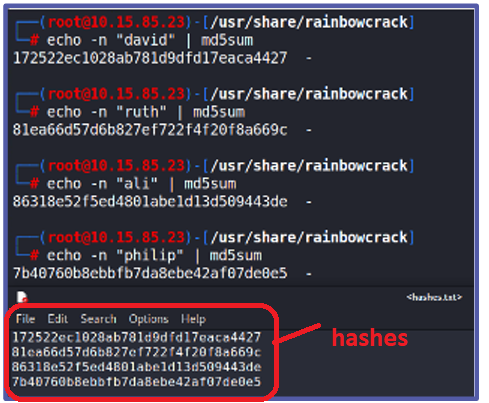
I circled the hash numbers.
Use nano instead
of leafpad in the instructions.
When you complete the assignment,
Enter the command of History.
Screen print the results.
Save the file as PX_lastname_HistoryRainbowTable.
Drop off both files into google classroom.
*********
*********
Due Date: September 13, 2024
D2.4.14LAB Brute Force Offline
Click here and follow the Lab instructions.
Follow the instructions below:
On page 13,
When you run john shadow --show
Screen print the output.
Save the file as PX_lastname_shadow.png
See example of hash image on the next line.

I circled the hash numbers.
Use nano instead
of leafpad in the instructions.
When you complete the assignment,
Enter the command of History.
Screen print the results.
Save the file as PX_lastname_HistoryBruteOffline.
Drop off both files into google classroom.
*********
*********
Due Date: September 16, 2024
D2.4.14LAB BruteForceOnline
Click here and follow the Lab instructions.
As you follow the instructions and get to page 17
This is what page 17 should look like:
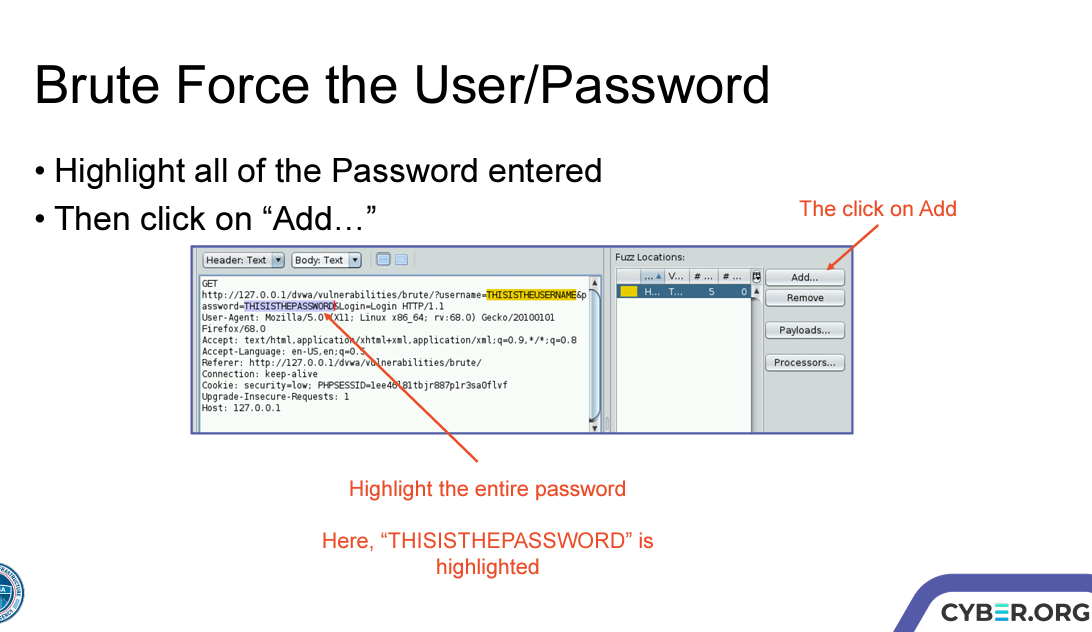
After you complete the instruction on this page,
Screen print it.
Save the file as PX_lastname_onlineBrute.png
When you complete the entire assignment,
Enter the command of History.
Screen print the results.
Save the file as PX_lastname_HistoryBruteOnline.
Drop off both files into google classroom.
*********
*********
*********
Resources you may need (Below)
*********
*********
*********
*********
*********
curriculum outline below: https://cyber.instructure.com/courses/100
*********
*********
Course Outline for Cyber Capstone
----------------------- August 25, 2024
Unit 1 - Actors/Motivations, CIA & Authentication
Unit 1 Lesson Plan
A2.1.1 - Threat Actors Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Stuxnet Quiz : Key
----------------------- August 25, 2024
B1.2.1 - CIA Triad and AAA Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
----------------------- September 3, 2024
C4.6.2 - Multifactor Authentication (MFA) Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Biometrics Quiz : Key
----------------------- September 5, 2024
D2.4.14 - Password Attacks Lesson Notes
PowerPoint Guided Notes Answer Key
D2.4.14Lab_A Passwords
D2.4.14Lab_B Rainbow Table
D2.4.14Lab_C Brute Force Offline
D2.4.14Lab_D Brute Force Online
H4.6.3 - Passwords Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Dictionary Quiz : Key
----------------------- September 13, 2024
Unit 2 - Social Engineering & Access Control
Unit 2 Lesson Plan
I2.2.2 - Principles of Social Engineering Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Influence Campaigns Quiz : Key
J2.2.3 - Phishing and Spam Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Credential Harvesting
Case Study - Salesforce Phishing Quiz : Key
K5.6.1 - Phishing Awareness Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Phishing Quiz : Key
L2.2.4 - Misinformation and Impersonation Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Hoaxes Quiz : Key
M2.2.5 - Watering Hole Attacks and Typosquatting Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Typosquatting
Case Study - Watering Hole Quiz : Key
M5.6.2 - Security Awareness Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Insider Threat Quiz : Key
Unit 3 - Threats &s; Attack Surfaces
Unit 3 Lesson Plan
N2.4.1 - Malware Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Malware Quiz : Key
P2.4.2 - Ransomware Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Ransomware
Case Study - FBI Response to REvil Ransomware Quiz : Key
Q2.4.3 - Trojans, Backdoors, and RATs Lesson Notes
PowerPoint Guided Notes
Answer Key
QQ.Lab - Trojan
RR.Lab - Backdoor
SS.Lab - RAT/Bot
Case Study - The TeaBot Malware Goes Global Quiz : Key
T2.4.4 - Viruses, Worms, Spyware &s; Adware Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
U2.4.5 - Keyloggers Lesson Notes
PowerPoint Guided Notes
Answer Key
UU.Lab - Intro to Keyloggers
VV.Lab - Keylogger Application Quiz : Key
W2.4.6 - Logic Bombs &s; Rootkits Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Logic Bomb Quiz : Key
X2.2.1 - Common Attack Surfaces Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Wireless Security Quiz : Key
Y2.4.8 - DoS and DDoS Attacks Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Denial of Service
Case Study - Botnet Quiz : Key
Z2.4.9 - DNS Attacks Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
A2.4.10 - Wireless, On-Path, and Replay Attacks Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Session Replay
Case Study - Wireless Disassociation Quiz : Key
B4.5.1 - Endpoint - Protocol &s; Email Security Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Heartbleed Quiz : Key
C4.1.2 - Wireless Devices Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Wireless Jamming Quiz : Key
D2.3.1 - Application Vulnerabilities Lesson Notes
PowerPoint Guided Notes
EAnswer Key Case Study - Race Conditions
Case Study - iPhone Integer Overflow Quiz : Key
F2.4.11 - Application Attacks Part 1 Lesson Notes
PowerPoint Guided Notes
GAnswer Key Lab - Directory Traversal
Lab - Privilege Escalation
Lab - Pass the Hash Quiz : Key
H2.4.12 - Application Attacks Part 2 Lesson Notes
PowerPoint Guided Notes
Answer Key
HH.Lab - Buffer Overflow
II.Lab - Command Injection
JJ.Lab - Intro CSRF
KK.Lab - CSRF Application
Case Study - Chrome Crash Catastrophe Quiz : Key
L.4.1.4 - Application Security Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
2.3.2 - OS and Web-based Vulnerabilities Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - SQL Injection DVWA
Lab - SQL Injection Juice Shop
Lab - XSS DVWA
Lab - XSS Juice Shop Quiz : Key
4.5.2 - Endpoint - OS &s; Monitoring Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
2.3.3 - Hardware and Virtualization Vulnerabilities Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - VENOM Vulnerability Quiz : Key
2.3.4 - Supply Chain, Zero-day, and Cryptographic Vulnerabilities Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Zero Day Attack Quiz : Key
4.1.3 - Mobile Solutions Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Geolocation Quiz : Key
2.4.7 - Physical Attacks Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
1.2.3 - Physical Security Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
Unit 4 - Cryptographic Solutions
Unit 4 Lesson Plan
1.4.2 - Encryption Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Linux Personal File Encryption
Lab - Windows 7 Personal File Encryption Quiz : Key
1.4.4 - Obfuscation and Steganography Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Obfuscation
Lab - Steganography
Case Study - Steganography Quiz : Key
1.4.5 - Hashing, Digital Signatures, and Blockchain Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
1.4.1 - Public Key Infrastructure Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
1.4.6 - Certificates Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Certificates Quiz : Key
1.4.3 - Cryptographic Tools Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
2.4.13 - Cryptographic Attack Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Collision Quiz : Key
Unit 5 - Vulnerability Analysis &s; Remediation
Unit 5 Lesson Plan
4.3.1 - Identifying Vulnerabilities Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - ip-ifconfig
Case Study - Pen Testing Quiz : Key
5.5.2 - Pentesting Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Bug Bounty Quiz : Key
4.4.1 - Monitoring Resources Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
4.4.2 - Monitoring Tools Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Wireshark
Lab - tcpdump Quiz : Key
1.2.4 - Deception and Disruption Technology Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Honeypot Quiz : Key
4.3.2 - Vulnerability Management Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
Unit 6 - Security Controls
Unit 6 Lesson Plan
1.1.1 - Security Controls Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
3.1.2 - Architecture Considerations Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
3.2.1 - Infrastructure Considerations Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
2.5.2 - Hardening Techniques Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Backdoor Removal
Lab - RAT Removal
Lab - Backdoor Shortcut Quiz : Key
4.5.3 - Endpoint - Firewall, IDS/IPS &s; Web Filter Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
3.2.2 - Network Appliances Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
2.5.1 - Mitigation Techniques Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
3.2.3 - Secure Communication/Access and Effective Controls Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - NordVPN Hack Quiz : Key
Unit 7 - Data Management
Unit 7 Lesson Plan
3.3.1 - Data Classification and Types Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Handling Sensitive Data Quiz : Key
3.3.2 - Data Sovereignty and Protection Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - File Hashing Quiz : Key
3.4.1 - Resilience and Recovery I Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
3.4.2 - Resilience and Recovery II Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
Unit 8 - Infrastructure &s; SecOps
Unit 8 Lesson Plan
3.1.1 - Architecture and Infrastructure Concepts Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Specialized Systems Vulnerabilities Quiz : Key
4.1.1 - Hardening Targets and Secure Baselines Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Exposure Through Cloud Misconfiguration Quiz : Key
4.6.1 - Access Management Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Quantum Cryptography Quiz : Key
4.7.1 - Scripting and Automation Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
Unit 9 - Incident Response
Unit 9 Lesson Plan
2.4.15 - Indicators of Malicious Activity Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Equifax Quiz : Key
4.8.1 - Incident Response Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Cuckoo
Case Study - Incident Response Quiz : Key
4.9.1 - Logs Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Metadata Quiz : Key
Unit 10 - Processes &s; Governance
Unit 10 Lesson Plan
1.2.2 - Gap Analysis and Zero Trust Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
1.3.1 - Business Processes Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
1.3.2 - Technical Implications of Change Management Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
1.3.3 - Documentation and Version Control of Change Management Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
4.2.1 - Data Asset Management Lesson Notes
PowerPoint Guided Notes
Answer Key Lab - Data Sanitization
Case Study - Data Destruction Quiz : Key
5.1.1 - Security Governance Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - The GDPR Quiz : Key
Unit 11 - Risk, Audits &s; Compliance
Unit 11 Lesson Plan
5.2.1 - Risk Management Lesson Notes
PowerPoint Guided Notes
Answer Key Case Study - Failure to Disclose Quiz : Key
5.3.1 - Third-Party Vendors Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
5.4.1 - Security Compliance Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key
5.5.1 - Audits and Attestation Lesson Notes
PowerPoint Guided Notes
Answer Key Quiz : Key