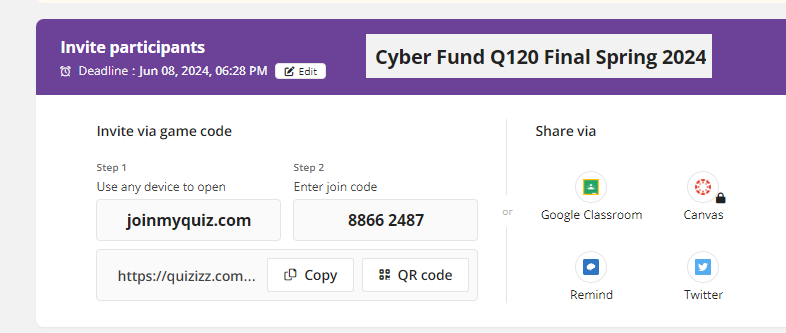
-Practice Quizizz for Fall 2024 Semester Final
Click here to practice the quizizz.
https://quizizz.com/join?gc=88662487

-Practice Quizizz for Fall 2024 Semester Final
Click here to practice the quizizz.
https://quizizz.com/join?gc=88662487

Due Date: May 13, 2024
Hardening your system Part 1
You need to practice this even if I am NOT present.
(I have told the substitue that you need to work on this first.)
Once you mastered this. Work on any remaining assignments.
WHEN I COME BACK WE WILL HAVE THE TEST.
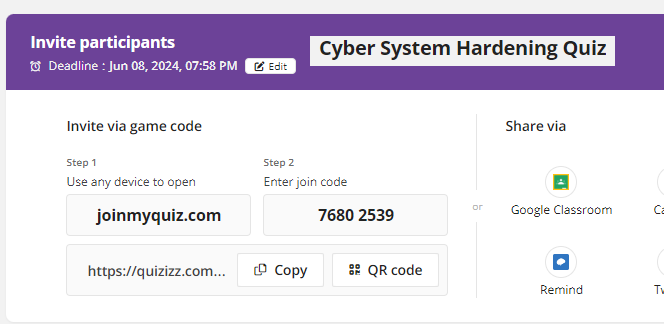
Assignment (System Harding Quizizz)
-Exam when I see you next.
-Click on this to access your quizizz.
https://quizizz.com/join?gc=76802539
Due Date: May 7, 2024
Unit 3 - Data Safety and Best Practices
3.1.2 - System Hardening Part 1
System Hardening
is the process of securing a system by
reducing its surface of vulnerability.
This involves configuring the system to
eliminate as many security risks as
possible by removing nonessential software,
unnecessary usernames or logins, and
disabling unused services.
Here are the key components and strategies
involved in system hardening:
Operating System Updates
Application Updates
Minimize Installed Software
User Account Management
Disable Unused Services
Firewall Configuration
Anti-Malware Tools
Encryption
Audit and Monitoring
Security Policies and Training
Lesson Guide
PowerPoint
Lab - MBSA Vulnerability Scan
Lab - MBSA Vulnerability Scan Answer Key
Lab - MBSA Vulnerability Scan PPT
Activity - Extension - Benchmark Selections Project
Activity - Extension - CIS Microsoft Windows 10 Benchmark Reference
Click here and Read System Hardening Lesson.
Click here and read the lesson Guide.
Copy the document found below into a google document.
Answer the questions in your google document.
Highlight the answer in yellow.
Name the the google document "Lastname - 3.1.2 - System Hardening Part 1"
Update Lastname to your last name.
Title: "3.1.2 - System Hardening Part 1".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Fundamentals
Lab - MBSA Vulnerability Scan.
-Locate your Cyber Range Passwords below by seat number.
Cyber Range Sign on ids and passwords (Period 1)
Click here and get your id and password.
Click here for your cyber range.
https://apps.cyber.org/login
-Using Linux and the python interpreter
If you have forgotten how to boot up your Kali Linux machine and run python.
Click here for full instructions.