Cyber Capstone
*********
*********
Data Sovereignty
is the concept that digital data is subject
to the laws of the country where it's stored.
Key issues include adherence to varying privacy laws like
the EU's GDPR, government access to data,
restrictions on international data transfers,
requirements for local storage of certain data types,
and debates over data ownership and control.
As digital data flows across borders,
companies and governments must navigate
these complex legal landscapes to ensure
compliance and protect stakeholder interests.
Due Date: May 2, 2024
2.1.2 Data Sovereignty and Protections
Teacher Notes - Read this.
Class note - Read this .
Copy the document found below into a google document.
Answer the questions in your google document.
Highlight the answer in yellow.
Name the the google document "Lastname 2.1.2 Data Sovereignty and Protections Guided Notes Answers"
Update Lastname to your last name.
Title: "2.1.2 Data Sovereignty and Protections Notes".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Fundamentals
Guided Notes Answer this.
Copy the document found below into a google document.
Answer the questions in your google document.
Highlight the answer in yellow.
Name the the google document "Lastname - 2.1.2 Data Sovereignty and Protections Quiz"
Update Lastname to your last name.
Title: "2.1.2 Data Sovereignty and Protections Quiz".
Modify the Standard heading with your information.
Amanda Success (Period 9)
Monday December 25, 2023
Seat 99 (Grade level 13)
Cyber Fundamentals
Quiz Answer here.
*********
*********
Due Date: May 2, 2024
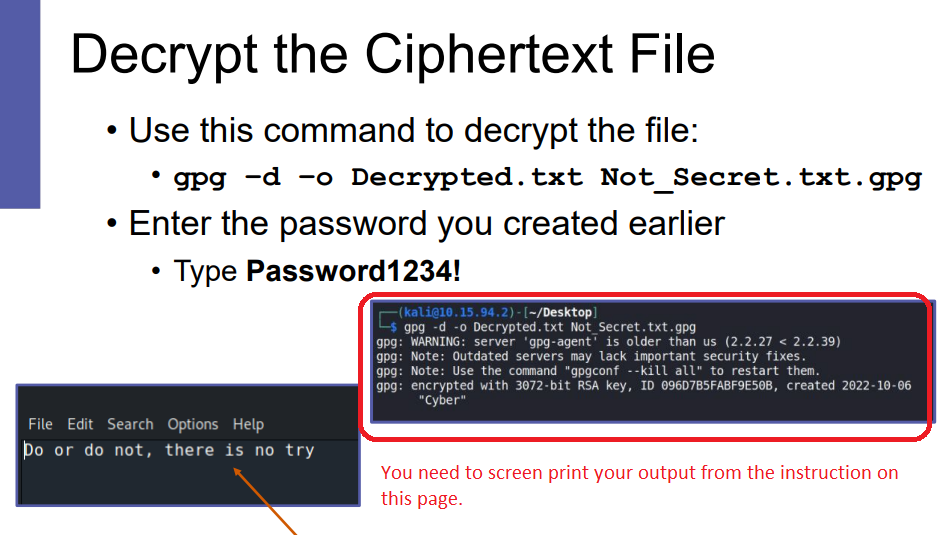
Click here for lab for Linux Personal File Encryption.
Your files are:
P1_LinuxEncryption_lastname1.png (History of Linux commands)
P1_LinuxEncryption_lastname2.png(2nd to last page of the exercise showing your result)
See sample output circled in red:
Drop them off too google classroom.
*********
*********
*********
*********
*********
*********
*********
Resources you may need and select Web address you may need (Below)
*********
*********
*********
*********
*********
Capstone
Unit 4 - Encryption and Cryptography
Unit 4 - Lesson Plan
2.8.4 - Crpytography Modes of Operation and Blockchains
2.8.5 - Block Ciphers and Lightweight Cryptography
2.8.6 - Steganography and Homomorphic Encryption
2.8.7 - Common Cryptography
2.8.8 - Cryptography Limitations Week of March 25
2.8.3 - Quantum Cryptography and Ephemeral Keys Week of April 1
3.2.3 - Database Security Week of April 8
1.2.16 - Cryptographic Attacks April 15
2.3.3 - Secure Coding Techniques April 22
2.1.2 - Data Sovereignty and Protection (week of April 28)
Unit 5 - Authentication and Security Protocols
Unit 5 - Lesson Plan
2.4.1 - Authentication Methods
2.4.2 - Biometric Authentication
2.4.3 - AAA and Multi-Factor Authentication
3.7.1 - Account Types and Identities
3.7.2 - Account Policies
3.8.1 - Account Authentication
3.8.2 - Account Access Control Schemes
2.7.1 - Physical Security Controls
3.1.1 - Secure Protocols
3.4.1 - Wireless Cryptographic Protocols
3.4.2 - Wireless Authentication Protocols
3.4.3 - Wireless Security Methods
3.4.4 - Wireless Installation Considerations Teacher Notes
Estimated Hours of all cyber areas
1. Linux Basics (20 hours)
2. Security Basics (35 hours)
3. Actors and Vulnerabilities (30 hours)
4. Malware and Attacks (60 hours)
5. Organizational Security (35 hours)
https://cyber.instructure.com/courses/243
Instructional Units
Sequence 1 Cyber course Cyber Fundamentals
Unit 1 - Foundations & Threats
• 1.0 - Cybersecurity Careers, course objectives and Ethics Agreement
• 1.1 - The CIA Triad and Authentication
• 1.2 - Identifying Security Threats
• 1.3 - Introduction to CLI (Command Line Interface)
Unit 2 - The Human Factor
• 2.1 - Social Engineering
• 2.2 - OSINT & Phishing
Unit 3 - Data Safety and Best Practices
• 3.1 - System Hardening
• 3.2 - IOT Threat Modeling
Unit 4 - Cryptography and Linux
• 4.1 - Bits, Binary and Encoding
• 4.2 - Basic Concepts of Cryptography
• 4.3 - Advanced Linux Command Line Interface
• 4.4 - Crypto Issues of Privacy vs Security
Unit 7 - Reconnaissance
• 7.1 Recon Introduction and Google Dorking
• 7.2 WHOIS and Nslookup
• 7.3 Network Scanning
Unit 8 - Network & System Threats
• 8.1 Net Attacks - Denial of Service (DoS)
• 8.2 Spoofing & Sniffing
• 8.3 Wireless, Mobile & VPNs
• 8.4 Pentesting & Exploits
• 8.5 Cyber War
Unit 9 - Online Threats
• 9.1 Basic Web Concepts
• 9.2 Web Vulnerabilities
• 9.3 SQL Database Attacks
Unit 10 - Encryption Security Tools
• 10.1 Symmetric & Asymmetric Encryption
• 10.2 SSL for Online Security
Instructional Units
Digitial Forensics
Sequence 2 Cyber course https://cyber.instructure.com/courses/243
Unit 5 - Devices and Networking
• 5.1 - Computing Devices
• 5.2 - Networking Fundamentals
• 5.3 - Protocols and Packets
Unit 6 - Law & Ethics
• 6.1 Impact of Law and Ethics on Cybercrime
https://cyber.instructure.com/courses/100
Unit 2 - Forensics (Digital Forensics)
- Extensive Linux Sessions
- https://www.cusack2.com/KCHS23_24/202404Apr/W01/03_Cyber/Cyber.html
Unit 13 - Network Security (Digital Forensics)
Unit 15 - Governance, Risk, and Compliance (Digital Forensics)
General outline of High Level
Cyber Capstone
Sequence 3 Cyber course Unit 0 - Teacher Resources.
Unit 1 - Intro to Linux
Unit 3 - Unit 3 - Password
Unit 4 - Encryption and Cryptopgraphy
Unit 5 - Authentication and Security Protocols
Unit 6 - social Engineering
Unit 7 - Threat Vector
Unit 8 - malware and Attacks Part 1
Unit 9 - Malware and Attachks Part 2
Unit 10 - Malware and Attacks part 3
Unit 11 - Malware and Attacks part 4
Unit 12 - Architecture and Design
Unit 14 - Mobile Devices and PKI